- Primus
- Products
- Defender
Defender
Revolutionizing Telecom Security with SIP Protocol Defense, Real-time Threat Detection and innovative Honeypot Data.
Sign up for a free 30-day trial*
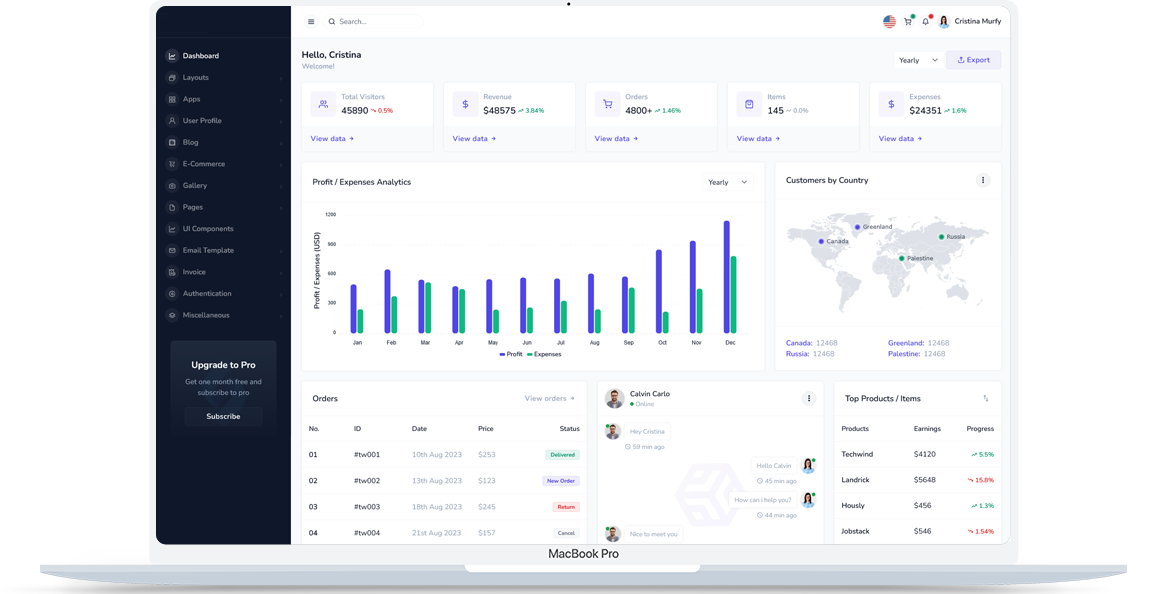
Ccutting edge, real-time telecom fraud prevention, ensuring the protection and integrity of your telecom network.
Defender harnesses the power of advanced SIP protocol analysis to identify and deflect fraudulent calls at their source, ensuring the integrity of your network.
Our state-of-the-art system is built to detect suspicious call patterns and behaviors in real-time, preemptively blocking unauthorized access to your network
Furthermore, it is advantageous when the dummy text is relatively realistic so that the layout impression of the final publication is not compromised.
Defender is your proactive defense shield. Benefit from automated responses that neutralize fraudulent attempts, reducing the risk of financial losses and maintaining your network's credibility.
Integrating Defender into your existing telecom infrastructure is a breeze. Our solution is designed to seamlessly integrate, enhancing your security posture without disrupting your operations.
Navigating through the complexities of telecom security has never been easier. Defender boasts an intuitive interface that empowers your team to manage and monitor security protocols effortlessly.
Whether you're a small enterprise or a telecom giant, Defender scales to meet your needs. Enjoy adaptive security that evolves with your network's growth.
Detect and track suspicious activity in real-time. Honeypot Intelligence provides you with valuable insights into the tactics and techniques used by fraudsters, allowing you to proactively defend against emerging threats.
Protect your servers and infrastructure from unauthorized access and fraudulent activity. By diverting malicious actors to our honeypots, you keep your network secure and reduce the risk of telecom fraud.
Our cutting-edge Honeypot Intelligence solution is a dynamic and proactive defense mechanism designed to outsmart hackers and protect your telecom infrastructure. Our honeypots, strategically positioned across the internet, continuously shift and adapt, revealing deceptive information to potential hackers.
The surge in cold-calling, coupled with the escalating loss of earnings for end-users, is intensifying the need for network carriers to proactively implement strategies to block fraudulent calls, a move already mandated by recent legislation in France, Canada, and the USA.
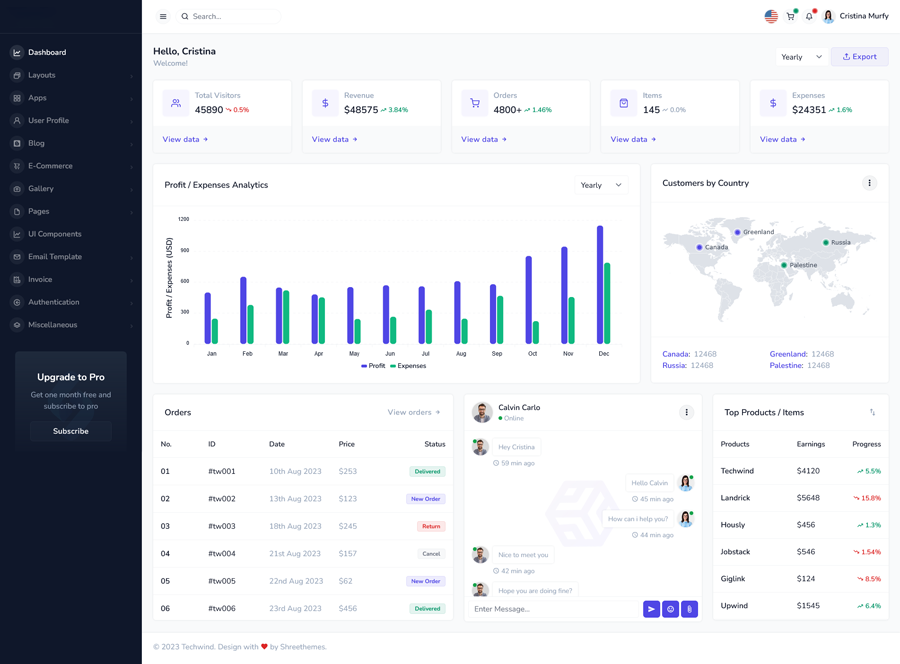
Our flagship product, Defender, integrates seamlessly into your network, using multiple metrics and cross referencing them with our intelligence database to determine if a call is potentially being made by a “Bad Actor”
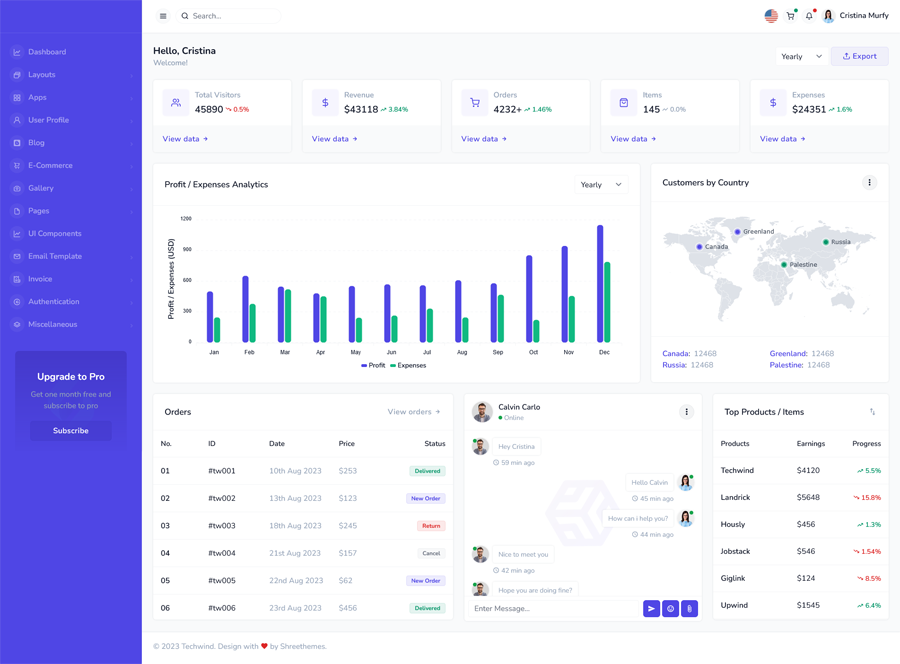
Our innovative Honeypot Intelligence solution provides a dynamic and forward-thinking defense tool engineered to outsmart hackers and safeguard your telecom infrastructure. Our honeypots, tactically placed throughout the internet, persistently evolve and adapt, acting as decoys to lure in potential fraudsters and reveal malicious actors before they even begin.
Start your free, no-obligation trial using Defender today and start blocking fraudulent calls to your network
See our pricingOur Defender pricing is based on the number of transactions per month. Get started now for your 30-day free trial*.
*Free trial subject to the terms outlined in our Fair Use Policy